Why the FBI needs no help from Apple
Sometimes I have difficulty writing headlines that don't reference livestock excrement so directly as to invalidate a story. That difficulty increases when it involves any statement made by the head of a police or espionage agency. Spies are liars. This is what they are paid for. Deception is the center of the profession of espionage and the FBI is a spy agency that occasionally dabbles in law enforcement.
The basics of the story are that the FBI is in possession of a locked iPhone belonging to San Bernardino shooter and federal prosecutors want to see if more people are involved. The FBI wants to force Apple, via an obscure 18th Century Law, to write a new version of IOS that will completely bypass the iPhone's somewhat robust security. There are solidly grounded fears that such a piece of software could be used on other phones at other times. There are other solidly grounded fears that such software requirements would lead to routine conscription of tech companies to undermine their own security and thus consumer confidence at home and abroad.
Apple's CEO Tim Cook issued an open letter to the public seeking support and calling the backdoor requirement a dangerous precedent. Ars Technica ran a story outlining the history of the the 1789 All Writs Act and Apple's probable legal strategy. Apple has already lined up top notch first amendment lawyers to make this into a free speech fight. The press generally is licking it's lips at the size of the wagon-load of grist destined for the mill and I'm calling BULLSHIT! Here is why:
The San Bernardino shooters are dead. As in dead and cold. They have been dead, done and colder than botched election results from 1948 for months. This was a terror attack on American soil, so the investigation of the dead couple has access to whatever resources it needs. Leaks to the press, peppered with such phrases “may-have” and “appear to have”, happen semi-regularly just so the FBI can remind us of their perception of their own relevance.
Dead people do not create new data and now the FBI thinks they “may” have had help. Being dead means doing nothing new, including not sending texts of making phone calls. So whatever data is on that phone, it was not made AFTER the shooting.
This is a national security investigation. It includes foreign connected actors carrying out lethal action on American soil. It is one of those rare cases where it is actually legal for the NSA to be involved. They definitely have access to every call or text sent to or from the offending phone. So whatever is on that phone, the NSA can get at it without physical access to the phone at all.
The FBI has already accessed all of that data and released it to the press. We know when they traveled, where they traveled, how they got there, what they said on Facebook. A great deal of computer forensics has been done on them and where the FBI is lacking in skills they have the talents of the most skilled agency in the world at their disposal. For instance according to the CBS affillate in San Bernardino: “While he has not been found on any terror watch lists, officials believe Farook was radicalized prior to committing the senseless and violent acts. He was reportedly in contact with people who may be linked to terrorism overseas.”
The FBI has wanted a general solution to iPhone encryption for some time. As reported by the Washington Post, FBI director James B Commey “blasted” the new iOS encryption scheme as soon as it came out in 2014. It is disliked because federal and local law enforcement have found themselves unable to violate privacy on whim or with a court order from a sympathetic judge.
Iphone encryption is not as strong as the public might be lead to believe. For commercial grade encryption, it is strong. A quick check of what iPhones are made of (I don't own one to disassemble) shows it to be running Advanced Encryption Standard, or AES. AES was certified by the Secretary of Commerce and the NSA in 2002. The NSA has a long history of pushing sub-standard encryption on the public through a program known as Operation BULLRUN.
NSA efforts to crack AES began years ago. Amongst the things revealed by Edward Snowden was a project to break AES called project TUNDRA. This was reported in Der Spiegel in 2014:
Several Academic attempts have been made to break AES. At least one, in a published paper, involved a side-channel attack on AES without administrator access to the device. It was termed computational infeasible, which means “can't be done with computers we can afford.” The amount of computing power needed to carry out this attack in a reasonable amount of time is within the NSA's budget.
Other implementations of AES, such as SSL, have been broken. The so-called “heartbleed” attack on SSL was used to cause Target's serious losses by hackers, and yet it is still used in voting machines today.
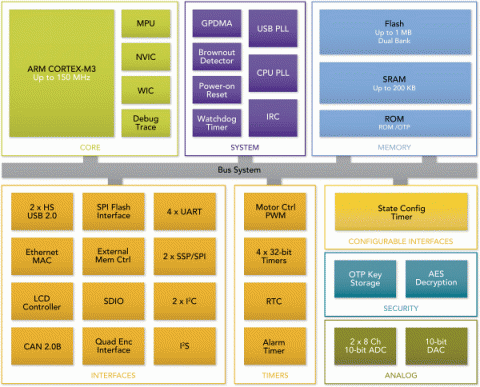
The encrypted memory of an iPhone is physically separate from the rest of the device. As the block diagram of an iPhone (below) shows, the physical component containg the security module and the memory are separate but attached to the same bus. Thus the actual encrypted data can be cloned and attacked without access to the iPhone. This architecture makes an attack using massively parallel computing systems feasible. This is method is what the NSA would likely use.
Given all these easily documented facts the FBI does not need a custom built version of iOS to break into a single phone. Given some background knowledge, and a little research, I was able to divine at least two ways to solve this problem that do not involve Apple and will likely cost less than the resultant court cases. Thus, Tim Cook is right, the FBI wants the backdoor and they want the precedent of forcing companies to make themselves
Given the relative feasibility of breaking into the offending phone, and the limited utility of a hacked version of iOS to the FBI or local law enforcement, something else is afoot. A court can order a defendant to unlock a device as part of a search warrant. The FBI's desired method would require physical access to the device. The whole exercise seems pointless until we look at other tools in the toolbox.
Combining a hacked version of iOS with an existent technology already used semi-legally is the real goal of the FBI. An iPhone hack is academic until installed remotely. Using already well-known cell-tower spoofing technology, called Stingray, the FBI could trick a targeted citizens phone into installing an operating system “patch” which is really their backdoor and then access the once-secure memory on that phone remotely.
The burden of proof to obtain a warrant to use Stingray is much lower. Stingray is considered a pen-register device, one that simply collects metadata including source, destination and time of call. A warrant application for a pen-register does not need to have probable cause. It only needs to state that it would be “useful” to an ongoing criminal investigation.
The FBI's line of attack leads inevitably to more spying, more warrant-less wiretaps, less privacy and less freedom. Tim Cook was right to call this a dangerous precedent. He was wrong to not see how actually dangerous it is.